Category: Technology
Guardians of the Living Flame – An In-Depth Analysis of Fire Alarm Systems
In the realm of safety and protection, fire alarm systems stand as vigilant sentinels, poised to detect and announce the presence of the relentless and destructive force of fire. These indispensable guardians, often overlooked in their ubiquity, play a critical role in safeguarding lives and property. In this in-depth analysis, we delve into the intricacies of fire alarm systems, exploring their components, types, and the crucial role they play in mitigating the devastating impact of fires. At the heart of every fire alarm system lies a network of sensors attuned to the slightest hint of smoke or heat. Smoke detectors, the unsung heroes of fire prevention, come in two main types – ionization and photoelectric. Ionization detectors excel in detecting fast-burning fires, while photoelectric detectors are more adept at sensing slow, smoldering fires. The synergy of these sensor types ensures a comprehensive coverage, providing early detection regardless of the fire’s nature. The auditory backbone of fire alarm systems, alarms and notification devices, assume the responsibility of alerting occupants to the imminent danger. Evolving beyond the traditional blaring sirens, modern systems incorporate voice evacuation systems, delivering clear and concise instructions to guide people to safety.

Visual signals, such as strobe lights, further enhance accessibility for those with hearing impairments. The integration of these elements transforms a fire alarm system from a mere alert mechanism to a comprehensive emergency communication system. Fire alarm systems are not one-size-fits-all instead, they are tailored to the specific needs of diverse environments. In residential settings, conventional fire alarm systems often suffice, relying on basic detectors and alarms. In contrast, larger and more complex structures, like commercial buildings or industrial facilities, demand addressable systems. Addressable systems pinpoint the exact location of an activated sensor, allowing for a rapid and targeted response by emergency personnel. This level of precision is instrumental in minimizing response times and optimizing evacuation procedures. The rise of smart technology has ushered in a new era for fire alarm installation san antonio, enhancing their capabilities and accessibility. Connected systems can be monitored remotely, providing real-time updates to building management or emergency services. Moreover, the integration of artificial intelligence and machine learning enables predictive analysis, allowing systems to anticipate potential fire hazards based on historical data and environmental conditions.
These advancements underscore the ever-evolving nature of fire alarm technology, as it strives to stay one step ahead of the unpredictable nature of fires. While the primary goal of fire alarm systems is prevention and early detection, their effectiveness is contingent upon regular maintenance and testing. Routine inspections ensure that sensors, alarms, and communication devices are in optimal working condition, ready to spring into action at a moment’s notice. Additionally, advancements in self-testing technologies empower these systems to perform automated checks, reducing the burden on human operators and guaranteeing a higher level of reliability. Fire alarm systems serve as the unsung heroes of safety, standing as the first line of defense against the ferocity of fire. Through a meticulous integration of sensors, alarms, and cutting-edge technology, these guardians of the living flame exemplify the pinnacle of fire prevention and mitigation. Their constant vigilance and adaptability underscore their indispensable role in safeguarding lives and property, making them an enduring cornerstone of modern safety protocols.
The Welding Standard – Elevate Your Quality Assurance
Quality assurance in welding is paramount for ensuring the integrity and safety of welded structures and components. The welding standard, a cornerstone of this assurance, plays a pivotal role in guiding welding professionals, manufacturers, and regulatory bodies towards achieving excellence in the welding industry. Welding standards are comprehensive documents that outline the specifications, procedures, and requirements for various aspects of welding, encompassing everything from materials selection to fabrication techniques and inspection processes. These standards provide a universally accepted framework that establishes consistency, reliability, and performance benchmarks for weldments in diverse industries, such as construction, automotive, aerospace, and energy production. The importance of adhering to welding standards cannot be overstated, as they not only help in minimizing defects and ensuring the longevity of welded structures but also have critical implications for the safety of individuals who interact with these structures.
A well-executed welding project, in compliance with the appropriate standards, can mean the difference between a secure and robust infrastructure and a potential disaster waiting to happen. Welding standards are not stagnant; they evolve in response to technological advancements, changing environmental factors, and emerging safety concerns. This adaptability ensures that welding practices remain relevant and effective in an ever-evolving world. Engineers, welders, and inspectors must stay informed about the latest updates and revisions in these standards to maintain a high level of competence and ensure that their work aligns with the most current best practices. Moreover, welding standards provide a foundation for effective communication among stakeholders. They offer a common language that facilitates collaboration between design engineers, welders, inspectors, and quality control personnel. This shared understanding of welding procedures and criteria fosters a sense of trust and reliability within the welding community.
The overarching goal of welding standards is to elevate the quality assurance across the industry, with a focus on precision, consistency, and safety. In summary, welding standards are the bedrock of quality assurance in the welding industry you can visit website. They serve as the guiding principles that drive excellence, safety, and efficiency in welding practices. Adhering to these standards ensures that welded structures and components meet stringent quality requirements, offering peace of mind to engineers, manufacturers, and the general public. As the welding industry continues to advance, welding standards will remain indispensable, continuously evolving to address new challenges and opportunities while upholding the highest levels of quality assurance. It is imperative for all welding professionals to embrace and elevate their commitment to these standards, not only as a best practice but as an ethical responsibility to ensure the well-being of society and the longevity of our critical infrastructure.
Who Can Help You Access the Dark Web on Chromebook?
Accessing the Dark Web on a Chromebook can be challenging, but it is not impossible. The Dark Web is a part of the internet that is not indexed by search engines, and it is often associated with illicit activities such as drug sales, weapons, and illegal pornography. It is important to note that accessing the Dark Web carries significant risks, as it is a hub for criminal activities, and many of the sites contain malware, viruses, or other harmful content. Therefore, it is essential to proceed with caution and take the necessary steps to protect your identity and data. One of the first things to consider when trying accessing the Dark Web on a Chromebook is the type of operating system you are using. Chrome books run on the Chrome OS, which is a lightweight, cloud-based operating system that is designed for web browsing and online productivity. While Chrome OS is secure, it does not offer the same level of customization and flexibility as other operating systems like Windows or Mac OS. As a result, accessing the Dark Web on a Chromebook requires some additional setup.

The first step is to download a Tor browser, which is a specialized browser that allows users to access the Dark Web anonymously. The Tor browser works by routing internet traffic through a series of servers, making it difficult to track the user’s location and identity. Another important step is to use a VPN Virtual Private Network to add an extra layer of security and anonymity. A VPN encrypts your internet traffic and hides your IP address, making it more difficult for hackers or government agencies to track your online activity. There are many VPN services available, but it is essential to choose a reliable and trustworthy provider that does not log your data or sell it to third parties. It is also important to be aware of the risks involved in accessing the Dark Web. Many of the websites on the Dark Web are illegal, and users who visit them may be subject to criminal prosecution.
Additionally, many of the sites contain malicious software or malware that can infect your device and compromise your data. Therefore, it is essential to exercise caution and avoid clicking on any suspicious links or downloading any files from unknown sources. Finally, it is important to note that accessing the hidden wiki Dark Web on a Chromebook may be against the terms of service of some websites or internet service providers. Therefore, it is recommended to use a separate device for Dark Web browsing, or to use a virtual machine to isolate your browsing activity from your main device. In conclusion, accessing the Dark Web on a Chromebook can be done, but it requires some additional setup and precautions. The first step is to download a Tor browser and configure it properly, including enabling the Tor network, installing security plugging, and using a VPN. It is also important to be aware of the risks involved in Dark Web browsing and to take steps to protect your identity and data. By following these steps and exercising caution, users can access the Dark Web on a Chromebook safely and anonymously.
The Guidelines To Get Rid of the Msvcp140.dll File Error Message
Considering that a DLL file error message could happen at basically any moment and, on the off possibility that it happens, the amount of incidences will turn into alarmingly far more subsequent until finally paid out, the apparently coherent reply of the finish customer is among one of anxiety. In fact, DLL file errors are honestly standard and easy to fix, provided that you have the right device to get it done.
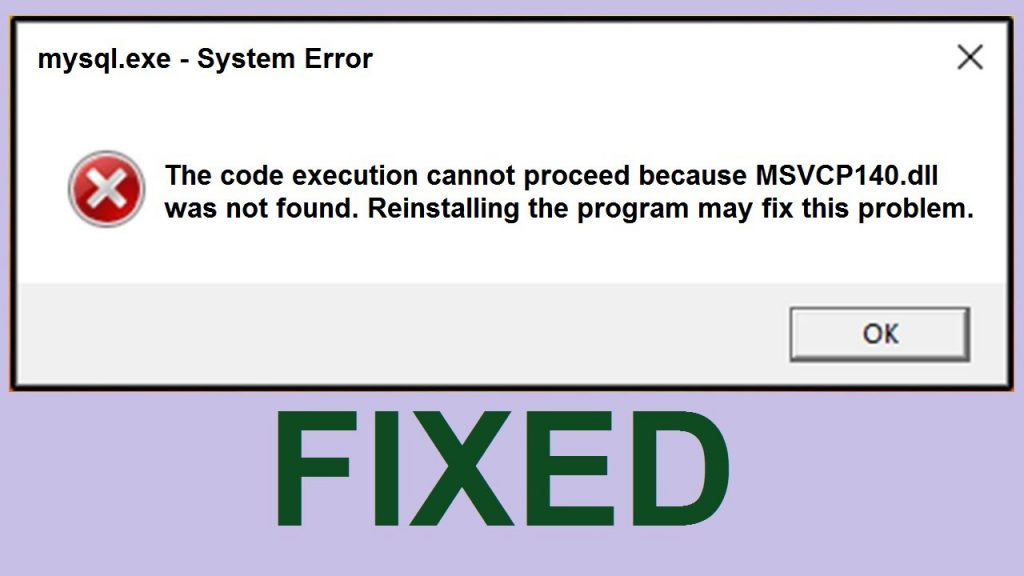
Justification Error
msvcp140.dll files will be the brand given to within a true feeling a lot of files on the PC that are accountable for practical use of regular files divided among the entirety of your respective PC frameworks. This way, whenever a DLL file is by the way migrated or erased during stacking and getting rid of projects, it has a cascading type of effect of probably debasing other DLL files as the framework registry wants the precise DLL which is as of this moment found it necessary to dispatch a program. In the event that the msvcp140.dll download might be notable and reinstalled, the platform will generally then reveal that there is certainly an additional DLL file error, since these files are unveiled in events and demand registry refreshes whilst reinstalling. Registry updates could be extremely harmful for your finish customer to endeavor, as being a standard error can for all those time harm the doing work structure, so is therefore exceptionally debilitate.
Breakthrough and Restoration
Even though it is not hard to discern a DLL error in the beginning from your alleviating back of the structure and ultimately at freeze up and the creation of the DLL file error message, it could not be not difficult to identify the specific DLL that is certainly creating the situation. Quite a few IT specialists will not endeavor to decide DLL file issues due to the truly amazing threat of platform registry harm. Nevertheless, the specialists which will handle the problem use an uncomplicated system that is open to the conclusion buyer. DLL files alter commonly and are normally provided as being a feature of program/OS refreshes. In the event that the DLL is explicit to application, fundamentally verify on the web with this present program’s changes.
At extended previous, several DLL fixes establish with issues together with the registry important passages concerning the file, rather than actual program, so utilize your PC fix apparatuses or registry cleaners to filtration system the Windows registry for missing parts, defilement, infection harm or symptoms of obsolete passages as an example employing file locations of before DLL adaptations. Providing the DLL file fix approaches saved right here neglect to assist you, installing DLLs should simply be completed utilizing traditional, deemed websites as a number of destinations do is out there that contains files with Trojan bacterial infections as a way to get these little bugs on your PC. Minus any additional exercise essential from the stop client, this device will, at that point as a result revise the framework registry and reestablish your PC to the exclusive usefulness.
Blockchain Investigations – Tracing Transactions with Computer Forensics
Blockchain technology has revolutionized the way we conduct financial transactions, offering transparency and immutability. However, it has also provided an avenue for illicit activities, prompting the need for blockchain investigations and the application of computer forensics techniques to trace transactions. Tracing transactions on a blockchain involves analyzing the publicly available transaction history and identifying the flow of funds between addresses. Each transaction is recorded on the blockchain, forming a chain of blocks, with each block containing a unique cryptographic hash. This inherent transparency enables investigators to follow the movement of digital assets. Computer forensics plays a crucial role in blockchain investigations by employing various techniques and tools to extract and analyze data from blockchain networks. The process begins with collecting information from the blockchain, which can be achieved by connecting to a full node or utilizing blockchain explorers and specialized software.

Once the data is obtained, forensic experts employ analytical methods to trace the flow of funds. They analyze the transaction history, examining the input and output addresses involved in each transaction. By following the digital footprints, investigators can link addresses to specific individuals or entities, unraveling the complex web of transactions. Furthermore, computer forensics techniques allow investigators to uncover additional information associated with blockchain transactions and investigate this page https://lifeviewresources.com/. This includes metadata such as timestamps, transaction amounts and transaction fees. By scrutinizing these details, investigators can gather valuable evidence that may aid in identifying and prosecuting individuals involved in illicit activities. To enhance the efficiency of blockchain investigations, advanced analytical tools and software are employed. These tools employ machine learning algorithms, data visualization techniques and pattern recognition to identify suspicious patterns, cluster related addresses and detect illicit activities such as money laundering or fraud. By automating certain aspects of the investigation process, computer forensics enables investigators to process large volumes of data and identify significant leads more quickly.
It is important to note that while blockchain technology offers transparency, it also poses challenges for investigators. The pseudonymous nature of blockchain transactions can make it difficult to directly link addresses to real-world identities. However, investigators can employ additional techniques such as blockchain forensics, which combines blockchain data with external sources of information to establish connections and uncover the identities behind the transactions. In conclusion, blockchain investigations rely on computer forensics techniques to trace transactions and identify individuals involved in illicit activities. By leveraging the transparency and immutability of blockchain technology, combined with advanced analytical tools and software, investigators can follow the flow of funds, gather evidence and unravel complex networks. As blockchain technology continues to evolve, so too will the methods and tools employed in blockchain investigations, ensuring a safer and more secure digital ecosystem.
How Does Buying Paper Shredder Will Be Worth Expenditure for Everyone
Regarding waiting have the option to shred massive levels of paper to help keep others from questionnaire fragile material. This benefits adding solutions in to a modern manufacturing paper shredder. In the same manner furthermore with different types of paper shredders they are equipped for cutting the paper into strips or very little sections. In spite of the reality that there is a handful of kinds of these machines that need simply a restricted volume of room, generally these machines in light in their dimension they require an enormous area. The establishment of a removal platform provides a much more clean operating weather conditions along with supporting with eradicating dust particles from the tool that slices the paper in to the expected pieces. With regards to the bailing platform this really is important to incorporate as it spots the paper in the small bunches approximately this time significantly less area is essential for receptacles where the paper should be stored.

Also with what you are considering acquiring with regards to a contemporary shredder for cutting up paper you ought to carry out some exam to the different models that are available. This way you can then discover which design with its variety of shows will satisfy your specific shredding requirements the most effective. These shredders usually are meant to cope with the middle of amount shredding that happens in locations like offices. When contrasted with home shredders, office shredders are larger, quicker and may work for a tremendous stretch out whenever as a result of engines within the machine. To safeguard an organization’s safety and increment its protection degree, just how is to buy an office shredder to cut up and obliterate magic formula reports, sensitive information or agreements. You are able to decide to shred papers into lace utilizing the strip-cut components or reduce paper into confetti-like pieces regarding the cross-cut product for additional well known stability.
Assume your business manages exclusive and categorized information and should deal with a lot shredding at times, it is suggested you get a tough primary paper shredder as opposed to the office form. When you go on a gander with the different types take into account how sensitive the material on the paper you happen to be coordinating off of is. On the away from chance that you simply believe so that it is very fine, decide on a model that shreds the paper into incredibly good parts. In fact individuals types that usage a cross cut instrument what slices the paper into fine sections need less space around the reasons that the items protected in the refute receptacle can be stuffed far more they really do are more expensive and find out more at https://afterprintltd.co.uk/. Although according to the modern industrial paper shredder that shreds the paper into pieces in most actuality do cost less however occupy far more room. Be that as it can, actually dealing with the shredder is significantly a lot more uncomplicated in truth the degree of assist they might require is widely much less contrasted together with the other.
Making Profits Online Is Definitely an Unexplored Part of the Cyber Community
The anonymity in the internet is really a dual-sided sword. It is extremely easy to start any sort of online business, which happens to be commonly referred to as ecommerce. Brands like Craig’s list and Amazon are founded models of how to earn money online. Anything and everything, and something similar to genuine physical businesses, may be changed about, to suit the surroundings from the cyber world, to earn money online. Most classic forms of companies are developing into online business trading markets. The possibility of this market is countless. Simply because first of all, comes about is the fact that business is ready to accept millions of individuals, that can run into your web portal and would want to work together with you. Therefore, an idea or concept is perhaps all that is needed, to generate income online.

The revenue getting potential of such websites depends mostly on the advertising. Slowly and gradually as being the sites set up on their own, they reinvent themselves to make money online. Be it the classified listings category like Quirk, or even the countless job research web sites like beast, all of them keep to the promoting design to generate income online. There is certainly obviously a poor side, to the cyber planet. There are many experts like hackers, online phishing agencies and in many cases seamstress that will promote hard, to bring in the unsuspecting website surfers, to sign up online, for supplying providers. Hacking and phishing are extremely serious and enormous distributed offenses, where the security of a web site, e-mail or possibly a banking accounts, is affected, and the true owner stands to reduce money. Nevertheless the phishers and the hackers make money online. This dark underbelly in the internet requires rigid cyber laws and regulations and powerful controls, to restrain the malpractices and exploitation of your simple customers of the internet.
Naturally the particular programs on what the complete internet survives particularly servers, website hosts, web designers, animators, programmers, technologists, website experts, online internet directories and also the online directory,, to the providers they supply. The internet agencies, the telecom leaders, as well generate profits online by providing connectivity every in which. There are numerous whirl-off industries, which live because of the online cash producers, who might seek to delegate work to such 3rd parties. Dark hat hackers, since they are known, are accountable for the grievous conclusion of hacking. These individuals wreck techniques out from wanton malice or to be able to ruin a opponent, and they people are generally the concentrates on of cyber security laws and regulations. A black color cap hacker can violate several laws and PersianHack regulations that are presently transforming descriptions to match the newest era of internet security and its particular connection on the rules. In summary, anybody can infer that, it should indeed be super easy to generate money online, for those who have an exclusive idea; only one will need to be cautious and employ only safe sites, to help make any purchases.
Why Utilizing Online Notes Sharing Become Well-Known today
Of the general enormous number of ways to deal with get-together opinions and client information presumably none are basically essentially as clear areas of strength for or a focal text message study. SMS studies are an extraordinarily immediate procedure for minding in any case various individuals as required with however various solicitations as you would like there is no affirmation that you will get a reaction from everybody notwithstanding. Luckily since such limitless individuals have telephones now the reaction rate on a SMS audit is absolutely high veered from common overviews. The idea driving a text survey is exceptionally clear. A SMS will be sent from a PC to any cell numbers picked. Precisely when the beneficiaries open the text message, they will see the solicitation you introduced then tolerating they also decide to answer their responses will be sent back to you.

Luckily the PC that sent the message outline is in addition fit neglected and recording all of the overview information and conglomerating it into the significant encounters. With an overview regardless the PC typically gets, figures, and sees all survey reactions. How this impacts you is that there could be right now not a need to really assess or record any information there are comparatively not any more tangled evaluations expected since the PC handles everything and read essential info here https://expobioargentina.com/why-we-need-to-stop-using-self-deleting-texts/. Text message outlines are altogether steady than by a wide margin most envision things, for example, able social events and games use SMS reviews too. A text, as a rule, message outline is just a procedure for getting examination or remarks on a solicitation paying little mind to what the point or scene. This plans that when the PC gets a response it can show you results the PC will keep on resuscitating as results come in too, making it conceivable to follow the outcomes as they occur.
In a standard study it will overall be clearly challenging to consolidate all of the survey information into a solitary source it requires an enormous extent of hypothesis. In the event that the information you are gathering is fabulously time precarious a SMS study may be a decent choice for you too. Considering the mechanized results PC seeing predictable analysis is direct to imagine. Generally, there truly is no other choice that can do everything online notes sharing can do. Text message audits are speedier and more effective than basically one more sort of overview not that they are similarly a lot simpler to utilize. Overlook the issue of coordinating and finding information results really the text message concentrate on PC will accordingly sort out anything you genuinely need, working on it to examine. Research text overview assists today and you with willing see something that obliges your own or business needs regardless of size or alternately aggregate’s expectations.
Reverse Phone Number Lookup – Something You Simply Need to Know How to Do!
There is no refuting the way that the broadcast communications industry has been a gift to all of us both old and youthful. In any case, similar to each and every thing in existence with each benefit comes a drawback. So it is at this point not something interesting to hear issues that has to do with instances of trick calls, trick calls and the preferences which are one of the weaknesses that accompanies the telecoms business. Before presently, managing these correspondence ills used to be a lot of issue, however on account of reverse phone lookup, we can now effectively handle all of these ills. Whenever you end up dug in for a situation of any of the above ills, or you essentially have to check a phone number, all you want to do is to search for a reverse phone lookup administration to join with. A lookup on an unlisted telephone number should be finished by doing a paid reverse phone lookup or search.

You might not have known about this previously yet do not stress we will check out at it in full. A reverse phone lookup administration is one that arrangements with getting every one of the subtleties that concerns a number and setting it up where we as a whole can undoubtedly get to it any time we need. The subtleties implied here incorporate the complete name of the number proprietor, their work records, criminal records to specify however a couple. As a matter of fact utilizing a reverse phone lookup resembles running an individual verification on the proprietor of that specific number. A reverse phone lookup is an approach to looking up who called me from this phone number. It will not be awkward to request you to secure help from a reverse phone lookup administration in light of crises.
Despite the fact that we are looking at settling the ills that accompany the phone business, a reverse phone lookup can likewise assist you with answers for different issues of life. For instance, in the event that you are going through your journal and end up finding a number that you did not pen down the name you can without much of a stretch utilize a reverse lookup to see who the proprietor is. Likewise, on the off chance that you end up being in doubt about a specific number that calls your accomplice, you can undoubtedly utilize it to cross check and see all that you want to be familiar with the individual. This is on the grounds that they will most likely come! Having the option to settle on a help to utilize is something that truly gives most people a migraine. This is on the grounds that, not every one of the organizations do what they maintain to do. Some of them are there to gather your membership charge and just that. This makes it exceptionally fundamental for you to choose a solid help to work with.

Minimizing Downtime – How Data Recovery Services Benefit Business Operations
June 18, 2024
Technology
Comments Off on Minimizing Downtime – How Data Recovery Services Benefit Business Operations
Sean Hernandez
In the fast-paced digital age, data has become the lifeblood of businesses, driving decision-making, operations, and customer interactions. However, with the increasing volume and complexity of data, the risk of data loss or corruption looms large, posing significant threats to business continuity and efficiency. This is where data recovery services play a crucial role in safeguarding businesses against potential disruptions and minimizing downtime. Data loss can occur due to various reasons such as hardware failures, software issues, human errors, cyber-attacks, or natural disasters. Regardless of the cause, the consequences can be severe, ranging from financial losses and operational disruptions to reputational damage and legal liabilities. For businesses, especially those reliant on critical data for daily operations, the ability to recover swiftly from such incidents is paramount.
Role of Data Recovery Services
Data recovery services specialize in retrieving lost or inaccessible data from storage devices such as hard drives, solid-state drives SSDs, servers, and even cloud-based systems. These services employ advanced techniques and technologies to recover data that has been accidentally deleted, corrupted, or rendered inaccessible due to hardware malfunctions or cyber-attacks.
Minimizing Downtime and Enhancing Productivity
One of the primary benefits of data recovery services is their capability to minimize downtime. Every minute of system unavailability can translate into lost productivity and revenue for businesses. By swiftly recovering critical data, these services help organizations resume normal operations without prolonged disruptions. This quick recovery process is particularly crucial for industries where real-time data access is essential, such as finance, healthcare, and e-commerce. Moreover, data recovery services contribute to enhancing overall productivity by enabling employees to focus on their core tasks rather than dealing with data loss aftermath. This ensures that business operations remain efficient and uninterrupted, fostering a conducive environment for growth and innovation.
Protecting Business Reputation and Compliance
In today’s interconnected world, maintaining customer trust and meeting regulatory compliance are non-negotiable for businesses. Data recovery services play a pivotal role in protecting business reputation by preventing data loss incidents from escalating into full-blown crises. By promptly recovering data, organizations can uphold their commitments to customers, partners, and stakeholders, demonstrating resilience and reliability in adverse situations. Furthermore, many industries are subject to stringent data protection regulations, such as GDPR in Europe or HIPAA in the healthcare sector. Data recovery services assist businesses in adhering to these regulations by ensuring that data is securely recovered and restored according to specified guidelines, thereby mitigating legal risks and potential penalties.
Cost-Effectiveness and Risk Mitigation
Investing in Data Recovery Blog is a proactive measure that can save businesses significant costs in the long run. The financial implications of data loss can extend beyond immediate recovery expenses to include lost revenue, operational delays, and potential fines. By minimizing downtime and swiftly restoring data, these services help mitigate these risks and protect the overall financial health of the organization. Moreover, outsourcing data recovery to specialized providers allows businesses to leverage expertise and resources that may not be available in-house. This ensures a more comprehensive approach to data protection and recovery, tailored to the specific needs and challenges of the business environment.